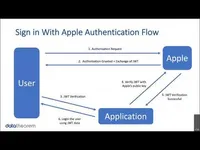
Exploit Analysis: Sign-in With Apple
Get a technical analysis of a recently discovered mobile exploit.
Get a technical analysis of a recently discovered mobile exploit. Eric Castro from Data Theorem breaks down how "Sign-in with Apple" was bypassed, which would allow hackers to take over a user's account in this week’s live demo.