Videos
Why Security Teams are Urgently Chasing API Security
25 mins
The Silent Threat: Uncovering the Vulnerabilities of APIs
Read More
How An Unsecured Server Led To A Microsoft Data Breach
20 mins
Learn how a cloud resource within the iOS Bing mobile app was left open on the internet, which is another recent example of a full stack application attack.
Read More
How Attackers Are Taking Advantage of Covid and Mobile Phishing
14 mins
How cyber security companies are seeing a huge uptick in mobile phishing due to recent reports of vaccines coming out to improve the pandemic.
Read More
What Is Full Stack Application Security?
1 mins
Learn what full stack application security truly is and how each layer is interdependent on another.
Read More
Introduction to Web Secure
8 mins
Data Theorem’s Web Secure product analyzes and protects single page applications (SPA), their embedded APIs, and underlying cloud resources.
Read More
How Modern Data Breaches Attack Every Layer of the Application Stack
15 mins
Review key findings from Verizon's 2020 Data Breach Incident Report (DBIR).
Read More
iOS Clipboard Spying
21 mins
Learn how your app developers can avoid accidentally capturing sensitive data from the iOS clipboard from their use of SDKs or third-party libraries.
Read More
How Integrated, Continuous Security Checks Can Save Your Business and Millions of Dollars
22 mins
How a recent data breach exposed 40 million private user records including geolocation and user photos of minors.
Read More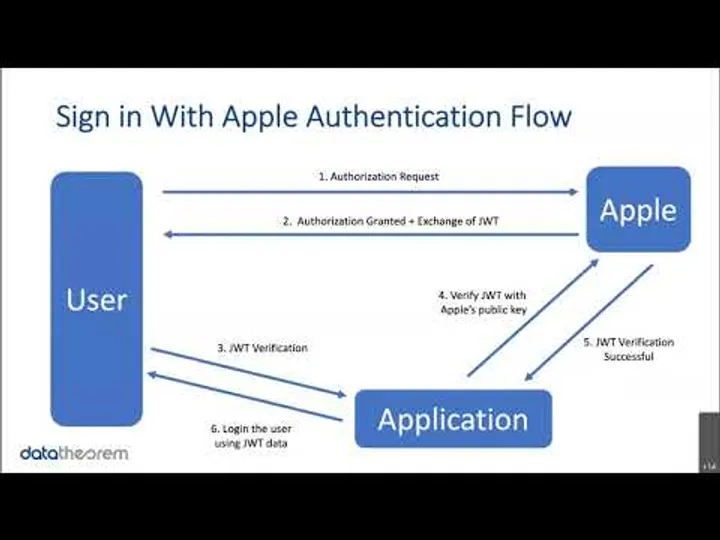
Exploit Analysis: Sign-in With Apple
18 mins
Get a technical analysis of a recently discovered mobile exploit.
Read More
How to Protect Application Attack Surfaces
18 mins
Learn how you can build a comprehensive security program that will automate key security policies across your entire data environment.
Read More
Live Demo: Case Study – Provident Credit Union
23 mins
Learn from our customer, Provident Credit Union, about how they manage their banking app with a 3rd party vendor, while protecting critical data.
Read More
Why Stop AppSec Data Breaches?
25 mins
Using recent data breach examples, we define an AppSec data breach, the risks involved with 3rd party software, and how to prevent them.
Read More
Introduction to API Secure
5 mins
Identify your entire attack surface by hacking your APIs, help you find shadow APIs, and better prepare you for securing your data.
Read More
Protect Web Apps from XSS Exploits
22 mins
Arm yourself with the knowledge needed to identify a cross-site scripting attack and secure your data.
Read More
Contact Tracing 101
14 mins
Learn about how contact tracing works, the proposed use of it, and how it will impact mobile privacy.
Read More
Inside Data Theorem’s Mobile AppSec Program
5 mins
Find out how Data Theorem’s automated mobile AppSec program works faster and more securely for your security and DevOps teams.
Read More
Automated Security for DevOps
2 mins
Data Theorem delivers automated security for DevOps, ushering in a new era of DevSecOps.
Read More
Customer Case Study: Evernote
3 mins
Data Theorem provides 100% security coverage of Evernote's entire mobile application portfolio with backend API services.
Read More
Data Theorem Interview Digital Anarchist RSA Conference 2019
11 mins
How we help customers with their data risk from mobile to API, assisting in the devops lifecycle.
Read More